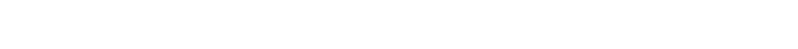Threat management offering
| Foundation (Typically 500 EPS) |
Stan Standard (Typically 1000-1500 EPS) |
Premium (Typically 1800-2500 EPS) |
|
|---|---|---|---|
| SIEM based 24x7 monitoring |
|
|
|
| ITSM with incident management |
|
|
|
| Use Case library aligned with MITRE attack framework |
|
|
|
| SOC KPI Dashboard Portal |
|
|
|
| Security orchestration Automated playbooks, Custom automated playbooks |
|
|
|
| Threat intelligence feed and Advisory |
|
|
|
| Malware Analysis |
|
|
|
| Threat Hunting |
|
|
|
| Behavioural Analytics |
|
|
|
| Brand Monitoring with Takedown |
|
|
|
| Threat Modelling |
|
|
|
| Incident Response and Forensics |
|
|
|
| Deep and Dark Web Monitoring |
|
||
| Deception |
| Foundation (Typically 500 EPS) |
Standard (Typically 1000-1500 EPS) |
Premium (Typically 1800-2500 EPS) |
||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Typical customer environment |
|
|
|
|||||||||||||
| SIEM based 24x7 monitoring | Shared SPOC for escalated incidents | Shared SPOC for escalated incidents | Dedicated SPOC for escalated incidents | |||||||||||||
| ITSM with incident management | ITSM portal access | Integration with customer ITSM supported | Integration with customer ITSM supported | |||||||||||||
|
|
|
|
|||||||||||||
| Use Case library aligned with MITRE attack framework | Sysmon logs | EDR and Sysmon enabled logs from servers | Deception alerts, EDR and Sysmon enabled logs from servers | |||||||||||||
| SOC KPI Dashboard Portal | Full access to widget library | Full access to widget library | Full access to widget library | |||||||||||||
| Security orchestration Automated playbooks, Custom automated playbooks | 2 standard integrations |
3 Standard integrations 2 Custom integrations 2 Custom playbooks |
3 Standard integrations 2 Custom integrations 2 Custom playbooks |
|||||||||||||
| Threat intelligence feed and Advisory | Free | Feed Integration supported | Deception based DNS attack monitoring | |||||||||||||
| Malware Analysis | 3 sample per quarter | 5 sample per quarter | 10 samples per quarter | |||||||||||||
| Threat Hunting | Once a week | Daily (Logs, TI, UEBA) | Daily (Logs, TI, UEBA And Deception) | |||||||||||||
| Behavioural Analytics (UEBA) | Using Logs and EDR | Using Logs, EDR, Network and End Point Deception | ||||||||||||||
| Brand Monitoring with Takedown |
10 takedowns a year 25 takedowns a year 200 takedowns a year |
Unlimited takedowns | ||||||||||||||
| Threat Modelling | Once a year | Twice Annually | ||||||||||||||
| Incident Response and Forensics | 50 Hours a Year | 50 Hours a Year | ||||||||||||||
| Deep and Dark Web Monitoring | STIX/TAXI Feed integration with SIEM | |||||||||||||||
| Deception | Network, End Point |
- * - Includes Two network sensors and 1000 endpoint decoys
- ** - Include access to Cyberrange training program for virtual hands on exercises to simulate Red team, Blue team exercises, Post Security Incident
- *** - AD integration includedResponse process. On Demand metered access to Cyberrange virtual environment throughout the year